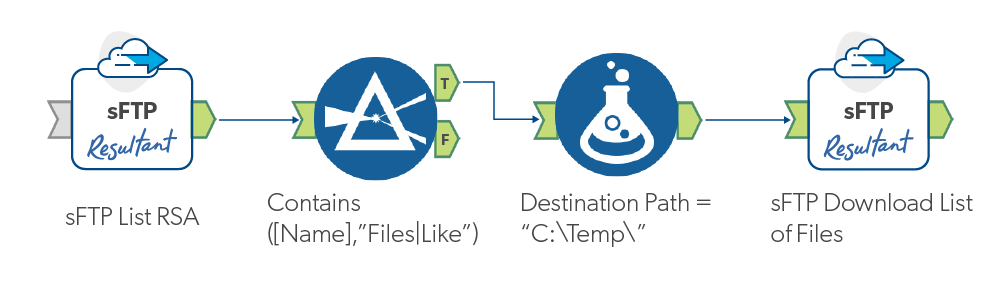
The first instance of the tool is in the “Block/None” mode and statically lists the contents of a directory. The second instance of the tool is in “Batch” mode and dynamically downloads any files that make it past the filter to the destination path.
If you need to upload files to an sFTP, you need to write them to disk first. They can be written to the [Engine.TempFilePath] so that Alteryx cleans up afterwards, but they must be on disk for the tool to transmit. It is not designed to take records on input and write those records to an sFTP destination.
Regarding the formatting of the fields: In all the tools, the required formatting of values in the static form is the same for the values passed in for “Batch” mode. The easiest way to work it is to use the static form in “Input/Block” mode until you get the desired result and use that understanding as the basis for what needs to be provided on the incoming stream in “Batch” mode. For the sFTP tool specifically:
sFTP Server: This is not a browser implementation like the download tool. As such, this is just the server name. No protocol, no port, no path.
“sftp://myserver.com:22/mydirectory” <= wrong.
“myserver.com” <= right.
sFTP Port: Port number only. Default is 22
Username: This is highly variable and depends entirely on what the host expects.
RSA Private Key: see explanation below in the thread.
Password: This is highly variable and depends entirely on what the host expects.
Remote Path: Use ‘/’ in this path for any separators as that is standard for FTP. If this path doesn’t have a ‘/’ at the end, the tool adds it when uploading or downloading. It does not add a trailing ‘/’ when using the list action, so the remote server implementation may behave differently with its inclusion or exclusion at the end.
Remove Path: This is a remote path and can be either a folder object or a file object but is a FULL path. Success or failure here is largely dependent on support for the action and your permissions on the remote server.
Local Path: Use ‘\’ in this path for any separators as that is what Windows expects. If this path doesn’t have a ‘\’ at the end, the tool adds it when uploading or downloading.
Filename: Just the filename and extension, no path.
NOTE
We are assuming the reason you found our tool, specifically the sFTP tool was the need to use an RSA token. The "BEGIN RSA PRIVATE KEY" packaging is sometimes called: "SSLeay format" or "traditional format" for private key. If you would really like to geek out for the afternoon, these are the relevant RFC documents regarding the RSA key format:
https://tools.ietf.org/html/rfc4716
https://tools.ietf.org/html/rfc5208
https://tools.ietf.org/html/rfc8017